- IT Services
- Penetration Testing
Penetration Testing
-
Pen testers (or ethical hackers) use the same tools and techniques as cybercriminals but with permission and in a controlled environment to improve an organization’s security posture.Core Concepts of Penetration Testing.
Core Concepts of Penetration Testing.- 1. Reconnaissance (Information Gathering)Initial phase where testers collect information about the target (e.g., IP ranges, domain names, exposed services) using tools like Nmap, WHOIS, and Shodan.
- 2. Scanning and EnumerationIdentifying open ports, services, and vulnerabilities. Tools like Nessus or Nikto are commonly used here.
- 3. ExploitationAttempting to exploit vulnerabilities discovered (e.g., SQL injection, weak passwords, unpatched software) to gain unauthorized access.
- 4. Post-ExploitationAssessing what an attacker could do after breaching the system — such as privilege escalation, data exfiltration, or lateral movement.
- 5. ReportingDocumenting findings with risk assessments, proof of concepts, and remediation steps. This is crucial for fixing issues and improving defenses.
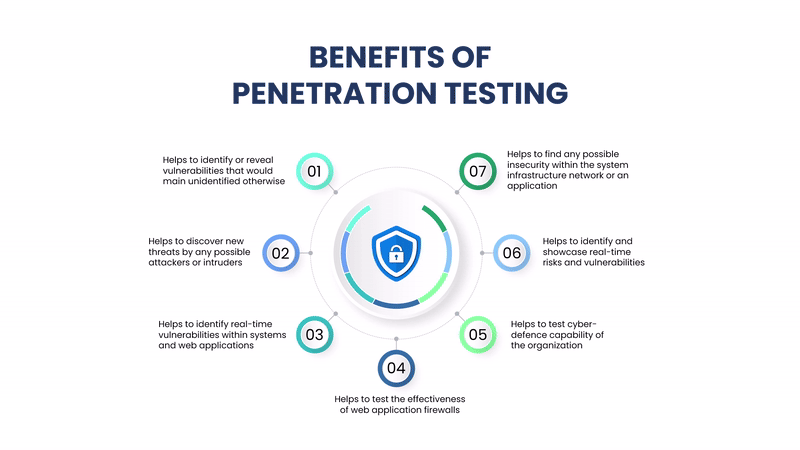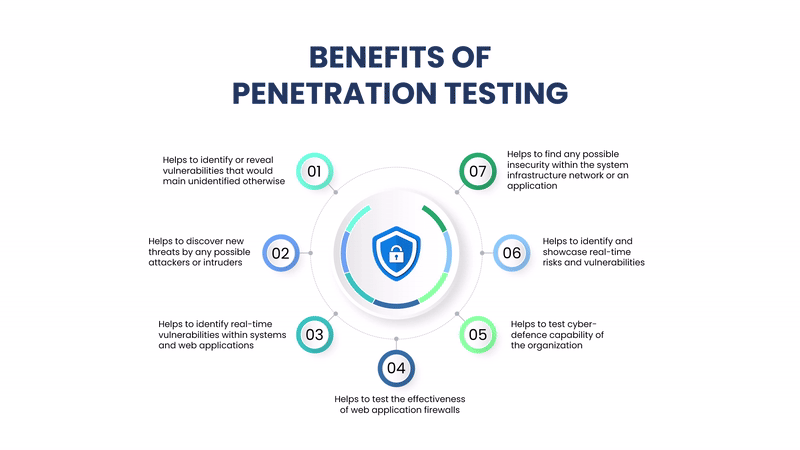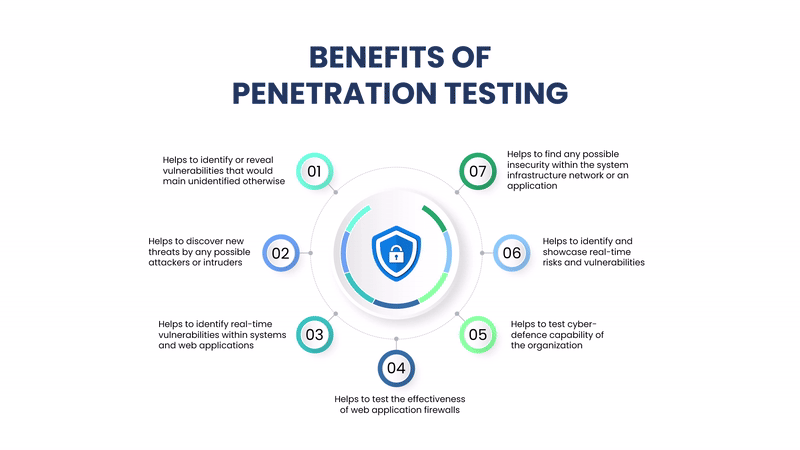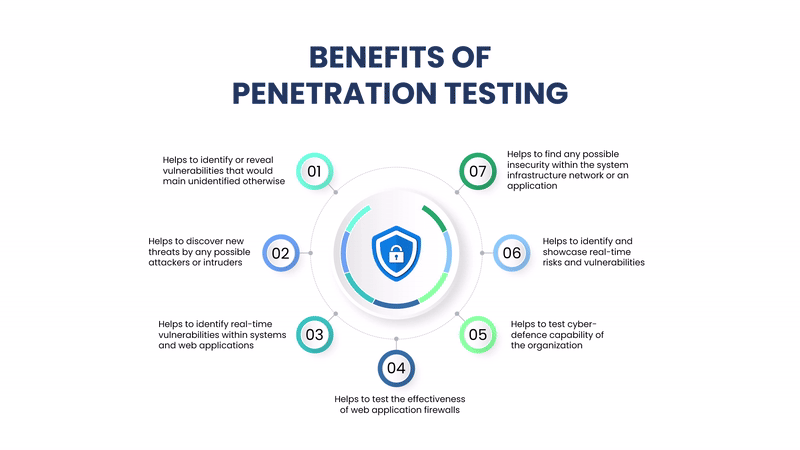
Benefits of Penetration Testing
Identify Security Weaknesses: Before attackers find and exploit them.
Compliance and Regulatory Needs: Helps meet standards like PCI-DSS, HIPAA, ISO 27001, and GDPR.
Improved Incident Response: Helps organizations refine detection and response capabilities.

Risk Management: Offers insights into real-world risks to inform better security investments.
Protects Brand and Trust: Prevents data breaches that could damage reputation and customer confidence.
Frequently Asked Questions
Is penetration testing legal?
Yes, when authorized by the organization being tested. It’s illegal to hack systems without permission.
How often should penetration tests be conducted?
At least annually, or after major changes in infrastructure, applications, or compliance requirements.
What are the different types of penetration testing?
-External Testing: Focuses on publicly exposed assets (e.g., websites, firewalls). -Internal Testing: Simulates an insider threat or a breach from within the network. -Web Application Testing: Targets web-based apps for common flaws like XSS, SQLi, CSRF. -Wireless Testing: Assesses security of Wi-Fi networks and connected devices. -Social Engineering Testing: Tests human vulnerability through phishing or impersonation.
What tools are commonly used in pen testing?
-Recon: Nmap, Shodan -Scanning: Nessus, OpenVAS -Exploitation: Metasploit, SQLmap -Post-exploitation: Mimikatz, BloodHound -Reporting: Dradis, Faraday
What’s the difference between penetration testing and vulnerability scanning?
Vulnerability scanning is automated and identifies known issues. Penetration testing involves manual effort to exploit vulnerabilities and assess real-world risk.

Is the huge volume of data is too hard to handle ?
Let us help you to give best solutions for enterprising data lake & data warehousing.
